IP (Internet Protocol): This is the main protocol that allows different computers to communicate with each other over the internet. It allows computers to send and receive data to and from each other, making communication over the internet possible. It’s like the postal system of the internet, delivering packets of data from one computer to another.
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol): These are transport protocols that work with IP to ensure data is sent and received correctly. TCP is like a courier service that guarantees delivery, while UDP is like regular mail - faster, but without any guarantee.
They ensure data is sent and received correctly. TCP provides reliable delivery, ensuring all data arrives in the correct order. UDP is faster and suitable for situations where speed is more important than reliability.
HTTP (HyperText Transfer Protocol) and HTTPS (HTTP Secure): These are used for transferring web pages across the internet. HTTP is like sending a postcard, where anyone can read it, while HTTPS is like sending a sealed letter, which is secure and can only be read by the recipient.
FTP (File Transfer Protocol): This is used to transfer files from one computer to another over the internet. It’s like a courier service specifically for packages.
SMTP (Simple Mail Transfer Protocol): This is used for sending emails, enabling communication over email. It’s like the postal service’s system for sorting and delivering mail.
SSH (Secure Shell): This is used to securely access and control remote computers. It’s like having a secure telephone line that only you can use. It provides a secure way to access and control remote computers, crucial for managing servers remotely.
DNS (Domain Name System): This translates human-friendly website names into IP addresses that computers can understand. It’s like a phone book for the internet.
DHCP (Dynamic Host Configuration Protocol): This automatically assigns IP addresses to devices on a network. It’s like a receptionist at a hotel assigning rooms to guests.
SSL (Secure Sockets Layer) and Firewalls are security measures. SSL encrypts data during transmission (like sealing a letter) and Firewalls act as security guards, controlling incoming and outgoing network traffic.
They provide security. SSL encrypts data during transmission, protecting it from being intercepted. Firewalls control incoming and outgoing network traffic based on predetermined security rules, protecting networks from threats.
- Proxy servers: They provide increased performance and security by acting as intermediaries for requests from clients seeking resources from other servers.
Without these protocols, we wouldn’t be able to browse the web, send emails, transfer files, or securely access remote servers. They work together to ensure data is transferred quickly, accurately, and securely over the internet.
How systems talk to each other and make magic happen.
Network protocols are a pretty key part of systems today, as no system can exist in isolation - they all need to communicate with each other.
That being said, a few smart folks developed 'protocols', which are nothing but an agreed upon method of communication between systems.
- That is, the format of the messages exchanged, their relative order and expected responses are standardized, to ensure that communication is seamless.
There are, of course, multiple types of network protocols; let's go over just a few of them:
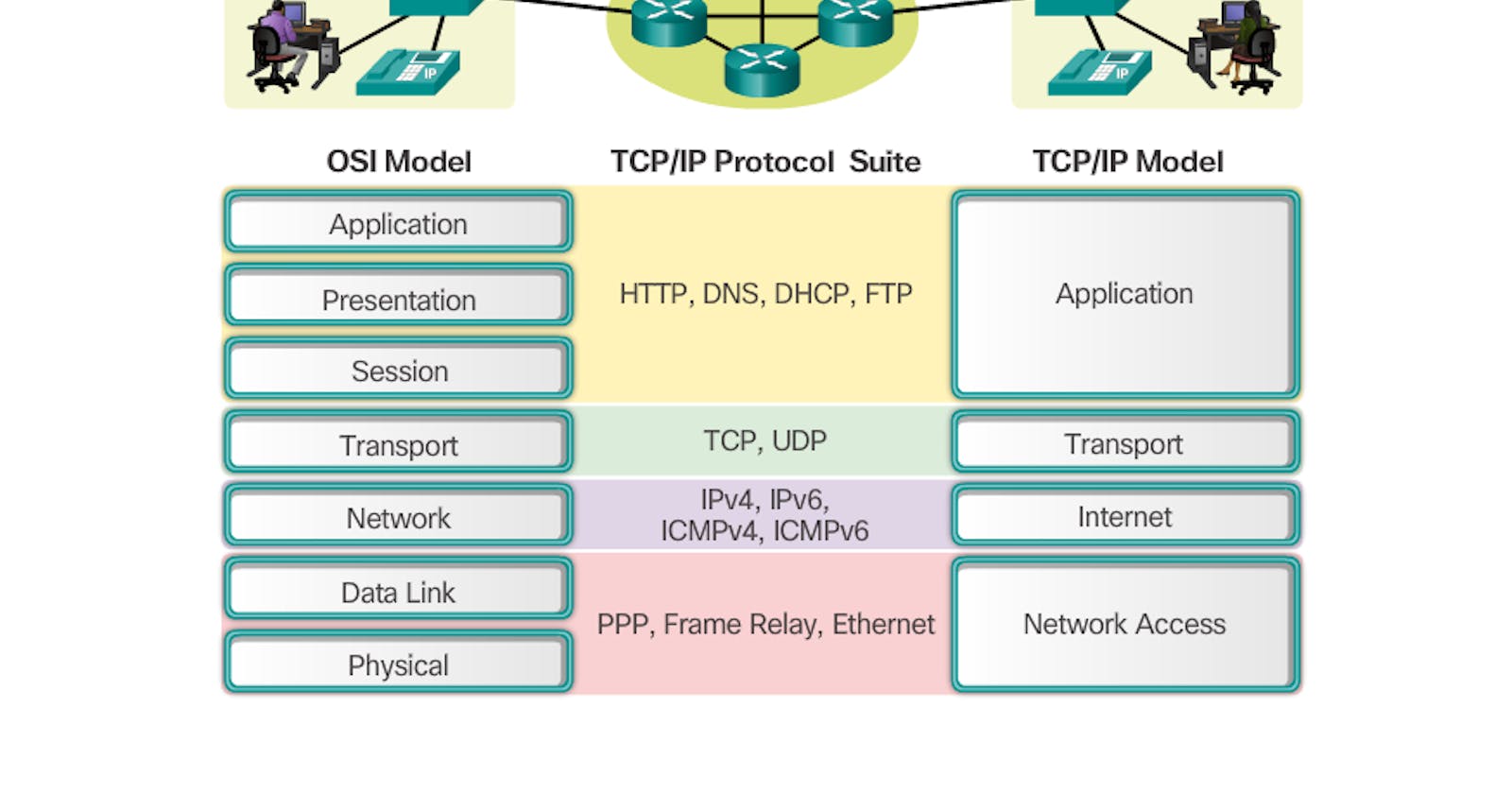
IP - stands for internet protocol; this network protocol outlines how almost all machine to machine communications should happen; other protocols like TCP, UDP and HTTP and built on top of IP.
TCP - stands for transmission control protocol; and is built on top of IP; this protocol is used in most web applications, and allows for ordered, reliable data delivery between machines over the public internet.
This is done by creating a connection on both ends (source and destination), and is usually implemented in the kernel, which exposes sockets to applications so that they can use them to stream data through the open connection
We usually hear the term 'handshake', and that typically refers to a computer sending a connection request to another computer; these connections need to be active, else they can 'timeout' or end based on some predefined criteria
3. HTTP - stands for hypertext transfer protocol; this is a very common network protocol implemented on top of TCP. As we saw with the client-server model, clients make HTTP requests, and servers respond with a response
- There are different 'methods' defined in a HTTP response, depending on how the data needs to be handled; as an example - GET (would retrieve data), POST (would provide data), DELETE (would remove data), and so on.
Requests typically have the following schema:
Host (string) - which would be a website, or server
Port (integer) - typically can be indicated by code which the server-clients create a connection over, depending on the nature of request
Method (string) - can be GET, PUT, POST, DELETE, OPTIONS or PATCH
Headers: defined based on the nature of request
Body: defined based on the nature of request
Responses typically have the following schema:
Status code (integer) - highlights the result of the response, again indicated through a standard set of codes
Headers: defined based on the nature of request
Body: defined based on the nature of request
Lastly, IP packets are effectively the smallest unit used to describe data being sent over IP, aside from bytes. They typically consist of:
An IP header, which contains the source and destination IP addresses, as well as other information related to the network
A payload, which is just the data being sent over the network
That about wraps it up for this one; network protocols usually work tirelessly behind the scenes of any modern system, and it helps to take a step back and understand what happens under the hood.